- Red Hat Community
- :
- Discuss
- :
- General
- :
- SELinux config for Django, Apache, MariaDB, Fedora...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 3,419 Views
SELinux config for Django, Apache, MariaDB, Fedora38 stack
Ok, I'm coming here after properly watching Thomas Cameron's lecture on SELinux and reading some other resources. https://youtu.be/_WOKRaM-HI4
I'm running Fedora 38 workstation inside a Vmware Workstation Pro (v17), with the rest of my stack being Apache, MariaDB, Python.
I have Django up and running on localhost:8000, I followed the configuration for mod-wsgi, Apache, Django properly. I have a virtualhost file to run my Django app on localhost:80 as well.
But I kept getting 500 internal server error. Turns out its a SELinux issue, since I did setenforce 0, and everything works fine.
Now I'm trying to troubleshoot whatever is making SELinux upset, so that I can turn it back on enforcing again. Its a local test server.
Please bear in mind that Fedora Documentation (new as well as the wiki) is still lacking significantly on this topic. So I couldn't get much over there. Nor there is anything related to SELinux on Django documentation.
I have setroubleshoot & setroubleshoot-server installed. Haven't been able to pinpoint the issue so far. I would appreciate if anyone can help me find what is causing the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 3,409 Views
Hi @SomeAB
What do you see in the logs when the error occurs?
Could you run "ausearch -i -m AVC -ts recent" when you get the error and paste the results here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 3,383 Views
here is the paste of my terminal output on `sudo sealert -a /var/log/audit/audit.log`
https://paste.pythondiscord.com/yujolenaze
and this is when I do `sudo ausearch -i -m AVC (-ts recent gave me no results)
https://paste.pythondiscord.com/acoyohapat
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 3,363 Views
Have you tried to run the command below?
"setsebool -P httpd_can_network_connect 1"
Please run it and them restart your application.
If it doesn't work, please share the new logs with us again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 3,315 Views
Hi @SomeAB !
Have you tried the suggestions from your logs :
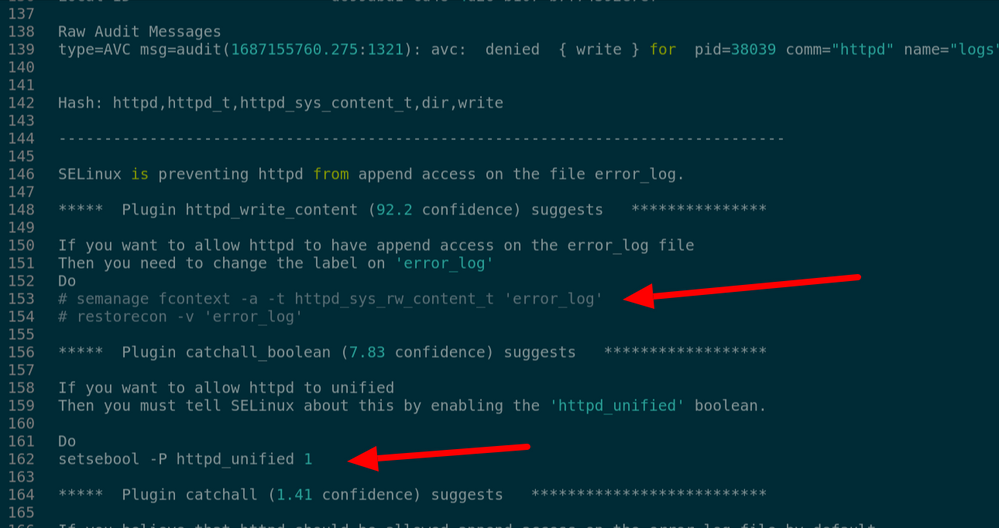
Try these : #semanage fcontext -a -t httpd_sys_rw_content_t 'error_log'
#restorecon -v 'error_log'
#setsebool -P httpd_unified 1
Then restart the httpd service.
If you continue to experience SELinux denials after trying these solutions, you can generate a local policy module using audit2allow to allow the specific access something lke this : ausearch -c 'httpd' --raw | audit2allow -M my-httpd ( but please be cautious in applying these solutions ).
Red Hat
Learning Community
A collaborative learning environment, enabling open source skill development.