- Red Hat Community
- :
- Red Hat Academy
- :
- Forum
- :
- Re: A couple of problems with RH134 (v9) chapter 8...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 4,027 Views
A couple of problems with RH134 (v9) chapter 8 labs - two cannot be completed.
RH134 (v9) Chapter 8, section 4 guided lab cannot be completed because of a known (?) bug in RHEL 9 that's been discussed elsewhere that prevents resetting the root password by breaking the grub bootloader.
Simply put, when trying to reset the root password, the system will not go into the root shell (the sh-5.1# prompt is never presented). Instead, it drops into emergency mode, which requires the root user's password, which is unknown (and the point of the lab).
The same bug affects Chapter 8, section 7 end-of-chapter lab. It, too, cannot be completed.
(A work-around is to log into the student account and then use sudo su - to log into the root user's account and change the password.)
---
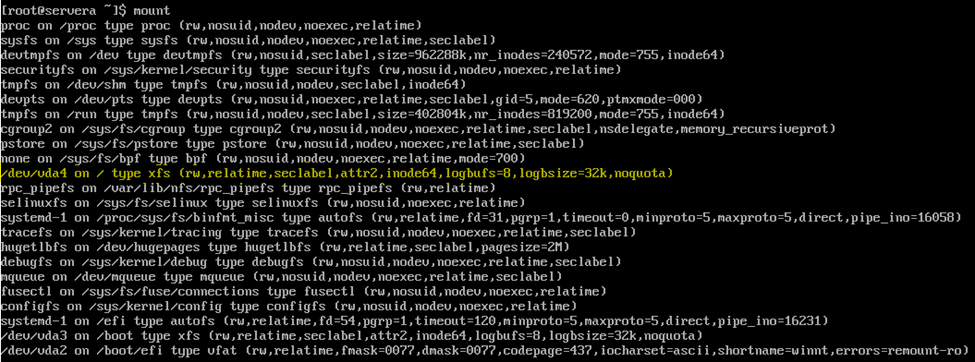
Another issue is this, from the Chapter 8, section 6 guided lab:
This is not true, It's never been true since RHEL started using systemd (RHEL 7). It doesn't not mount / as ro. It mounts is as rw, as seen here:
(This was screenshotted while performing the lab.)
I filed a Bugzilla report (here) about this a while back. It was closed on 02DEC2021 with this:
RHEL Program Management 2021-12-02 07:27:04 UTC
"After evaluating this issue, there are no plans to address it further or fix it in an upcoming release. Therefore, it is being closed. If plans change such that this issue will be fixed in an upcoming release, then the bug can be reopened."
Since it is not going to be "fixed," the content in the RH134 class should be changed, as it is incorrect.
Estrella Mountain Community College
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 4,015 Views
I use the following alternative solution to recover the root password:
- At the default prompt, press e
- At the end of the line that starts with linux, add 'init=/bin/bash'.
- Press Ctrl+X to continue
- Remount / with rw options: mount -o remount,rw /
- passwd root
- Relabel all files with SELinux context: touch /.autorelabel
- Change the current PID (/bin/bash) into systemd:
- exec /sbin/init #OR
- exec /usr/lib/systemd/systemd
Since the objective is to recover root's password, is suppose the method applied is of secondary importance.
I hope this can be helpful as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 3,997 Views
I tried this on one on servera, the system that the lab says to use. Unfortunately, it didn't work. What's worse, it locks up the system to the point that it cannot be restarted with Ctrl+Alt+Delete or by using rht-vmctl restart servera from foundation0. (Apparently, it completely stops systemd.)
I had to use the Virtual Machine Manager from foundation0 to regain control of the system using a force reset.
So, in the classroom and in *ahem* other situations where there is a servera or similar systems, this method does not/may not work.
Additionally, the RH134 material has the "traditional" way of resetting the password. Because of this, Chapter 8 sections 4 and 7 labs cannot be completed.
-----
Your method worked just find on a regular RHEL 9 intallation.
Estrella Mountain Community College
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 3,976 Views
To be honest, I didn't try it in an RHA Lab Environment, but on a KVM RHEL9 Virtual Machine, where it does work.
Indeed, when doing the lab, I discovered to my dismay that the procedure doesn't work, as you point out.
BTW, your workaround might work on a system where you have sudo rights as a regular user. I have yet to take the cert exam, so I am not sure whether we have such rights..
Unfortunately, chapter 23 of the RHEL9 Manual, Configuring Basic System Settings, mentions 'rd.break' as the solution to be applied.
Thanks for reminding me again to check and double-check
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 3,974 Views
Hello to everyone who is interested in root password recovery in a RHA lab environment!
I couldn't let it go, so tried just one simple procedure change:
Instead of applying 'e' to the first line on the grub2 screen, I applied it to the 'rescue' line. All the next steps work indeed as mentioned on the documentation page of RHEL9 and in the lab instructions on RHA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 3,815 Views
A bit of an update: RHEL 9.1 fixes this. I'm guessing that there will be an update to the Academy's images before too long.
(Incidentally, after reading the Bugzilla reports, it appears that this was intentional with RHEL 9, but after a number of reports, they put it back the way it was.)
Estrella Mountain Community College
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 3,766 Views
@Deanna hey, Deanna - is there anyone from Curriculum in the group that could have a look at these reports?
Best,
Tudor
Red Hat
Learning Community
A collaborative learning environment, enabling open source skill development.