- Red Hat Community
- :
- Archive Master
- :
- Red Hat Academy (Archived)
- :
- RHEL 8, RH134, Chapter 1 issues
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- 1,634 Views
RHEL 8, RH134, Chapter 1 issues
RHEL 8, RH134, Chapter 1 issues:
In Section 1, it states this:
Then, in Section 2 there's this:
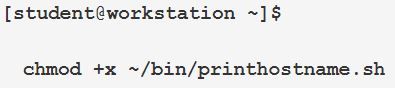
Then, in Section 4, there's this:
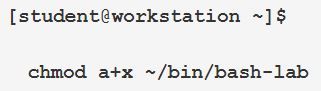
Then in Section 7 there's this:
Each example from Sections 2, 4, and 7 run contrary to the content presented in Section 1 because they allow any user to execute the script. (I realize that the scripts are limited to which users can execute them because of the directory they're in.)
The content says, "Grant execute permission only for the intended users of the script." This makes sense from a security standpoint.
All three lab examples indiscriminately grant execute permissions to everyone (world-executable). IMHO, this is a bad habit to teach student.
As a result, I'd suggest that each of the three lab examples be changed to, to keep in alignment with the content:
chmod u+x <script_name>
---
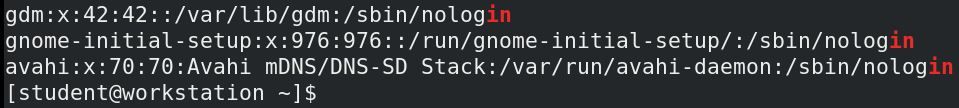
Section 5 has this:
The second sentence is technically true, but only because the regular expression is malformed. The $ doesn't go before the search string, it goes after: cat$
Here's the proof:
There are plenty of lines the end with in, but using a regex of $in won't find them..
Estrella Mountain Community College
Red Hat
Learning Community
A collaborative learning environment, enabling open source skill development.