- Red Hat Community
- :
- Discuss
- :
- Containers, DevOps & OpenShift
- :
- DO188
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 1,661 Views
DO188
Hello everyone,
I'm really confused about when should i use sudo podman or elevate the privilege to run a container or create image from containerfile.
I've few cases to ask about if i need to escalate privileges:
1-If i'll expose port 80
2-If i'm using mariadb and it is required to connect to the db as root user
3-when i should use sudo with the podman build or podman push command?
4-if i'm building image from containerfile and i need to install pkg or create user within the file shall i use sudo podman build?
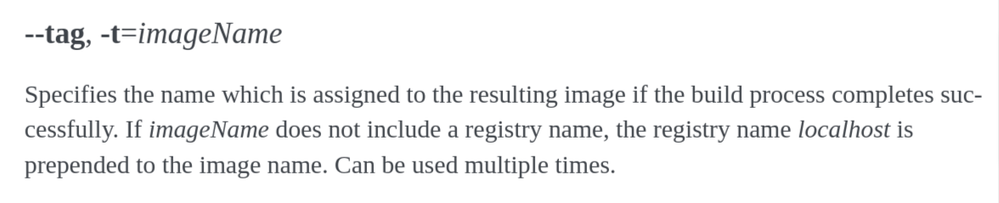
5-can i use command podman build -t quoay.io/imag_name or i need to tag it first with any tag without the registry name then use podman tag?
6-if i will commit a container to an image can i commit it with registry_name/image_name:tag and then push it to the registry with the same name?
Please metion all cases when i'll need to use sudo podman command.
Thanks i appreciate your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 1,614 Views
@khokha Thanks for reaching out.
I hope the below helps:
If you are exposing a port less than 1024, you should run podman as the root user or with sudo privileges.
If you are using MariaDB and it is required to connect to the database as root user, you can use sudo to run the command.
You should use sudo with the podman build or podman push command if you do not have root privileges.
If you are building an image from a containerfile and you need to install a package or create a user within the file, you should use sudo podman build.
You can use the command podman build -t quoay.io/imag_name to tag the image and push it to the registry with the same name.
Yes, you can commit a container to an image with registry_name/image_name:tag and then push it to the registry with the same name.
Please note that using sudo with podman is not recommended in most cases. It is better to use podman as a non-root user whenever possible.
Anyone, please correct me if I am wrong.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 1,522 Views
Hello @khokha !
Thanks for reaching out!
You might need to run podman with sudo in the following cases : Remember that running containers with root privileges is a security risk : we have workarounds there -
1. Podman will fail to start the container if the image uses multiple users and Podman does not have enough ID mapping to map the user and group IDs inside the container to non-root users and group IDs on your system. When you start the container as root, Podman uses your system's root user for the root user inside the container.
2. Applications such as HTTPd and Nginx are non-trivial to containerize for rootless use ( Red Hat provides containerized versions of HTTPd and Nginx that do not require root privileges)
3. Rootless containers cannot bind to privileged ports, such as ports 80 or 443 ( always use port forwarding )
However, you can use /etc/sysctl.conf for tuning system to use privileged ports by rootless containers : "net.ipv4.ip_unprivileged_port_start=79"
4. Rootless containers cannot use privileged utilities like ping utility, you can specify a range of group IDs that are allowed to use the ping utility by using : "net.ipv4.ping_group_range=0 2000000"
5. You cannot change the system clock by simply setting a SYS_TIME capability inside a container and running the network time service (ntpd), You would have to run that container as root.
Refer this for more detail https://github.com/containers/podman/blob/main/rootless.md
For your point 5 :
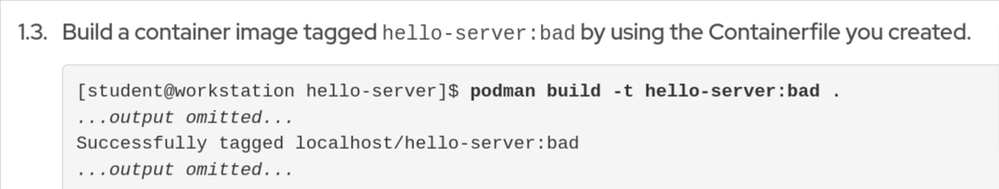
or you can build the image and then tag it using podman tag and then push it using podman push - your choice. Podman build takes two arguments: -t name[:tag] directory .
Yes to point 6.
FOr the mariadb part : Create a dedicated user with tailored access for your specific needs. This approach is generally safer than granting full root privileges. But if you absolutely require root access within the container for MariaDB, I think you can avoid using sudo by setting the MARIADB_ROOT_PASSWORD environment variable when launching the container. This allows secure root access with a dedicated password, without granting root privileges on the host system.
******************************************
Example :
The following container image uses the root user to start an HTTP server:
FROM registry.access.redhat.com/ubi9/ubi
CMD ["python3", "-m", "http.server"]
However we can tweak the containerfile so that it does not require elevated root privileges :
FROM registry.access.redhat.com/ubi9/ubi
RUN adduser \
--no-create-home \
--system \
--shell /usr/sbin/nologin \
python-server
USER python-server
CMD ["python3", "-m", "http.server"]
Red Hat
Learning Community
A collaborative learning environment, enabling open source skill development.