- Red Hat Community
- :
- DO280 - Red Hat OpenShift Administration II - Operating a Production Kubernetes Cluster
- :
- Forum
- :
- Re: DO280 ch06 LimitRange Vs Quota
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 5,218 Views
Hello,
I don't understand the difference between limit ranges and quotas.
I know limit ranges apply to pods, containers,... and both are used to set restrictions on resources consumption.
But i can set limits on no.of pods using quotas, so why do i need limit ranges?
One more questions:
what is the difference when i use webconsole:
1- workloads->deployments->actions->edit resource limits and
2- administration->limit ranges
won't they apply the same thing?
Thanks in advance
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 5,198 Views
Hello @khokha !
Thanks for reaching out!
In the most simplest of terms :
1. Quota ( ResourceQuota ) is for limiting the total resource consumption of a namespace. It is helpful when you need to prevent a single namespace from consuming too many resources and impacting other namespaces on the cluster.
Refer : https://kubernetes.io/docs/concepts/policy/resource-quotas/
2. LimitRange is for managing resource constraints/limitations at a pod and container level within the project. It is helpful when you need to prevent a single pod or container from consuming too many resources and hogging the cluster.
Refer : https://kubernetes.io/docs/concepts/policy/limit-range/
Now , why LimitRanges ? Compared to quotas , limitranges has more flexibility and granularity - how ? Quotas cannot be migrated as far as I know , but limitranges can be.
At the same time limitranges can be used to enforce limits on resources other than the number of pods. Meaning you can fine tune different pods inside a namespace as per their resource requirements.
An individual Pod or Container that requests resources outside of these LimitRange constraints will be rejected - from Administrator's perspective this is extremely critical / important to have a logical and efficient utilisation of resources at pod's level.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 5,199 Views
Hello @khokha !
Thanks for reaching out!
In the most simplest of terms :
1. Quota ( ResourceQuota ) is for limiting the total resource consumption of a namespace. It is helpful when you need to prevent a single namespace from consuming too many resources and impacting other namespaces on the cluster.
Refer : https://kubernetes.io/docs/concepts/policy/resource-quotas/
2. LimitRange is for managing resource constraints/limitations at a pod and container level within the project. It is helpful when you need to prevent a single pod or container from consuming too many resources and hogging the cluster.
Refer : https://kubernetes.io/docs/concepts/policy/limit-range/
Now , why LimitRanges ? Compared to quotas , limitranges has more flexibility and granularity - how ? Quotas cannot be migrated as far as I know , but limitranges can be.
At the same time limitranges can be used to enforce limits on resources other than the number of pods. Meaning you can fine tune different pods inside a namespace as per their resource requirements.
An individual Pod or Container that requests resources outside of these LimitRange constraints will be rejected - from Administrator's perspective this is extremely critical / important to have a logical and efficient utilisation of resources at pod's level.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 5,142 Views
Thanks for your reply @Chetan_Tiwary_
I've another question in review#1 step 3.1
Is there cluster-role called admin??
Isn't this role 'admin' at project level?
for the self-provisioner role if it is required in the exam to delete it , shall i use the command
"oc annotate clusterrolebinding/self-provisioners --overwrite rbac.authorization.kubernetes.io/autoupdate=false" to make coonfiguration persistent?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 5,133 Views
Hello @khokha !
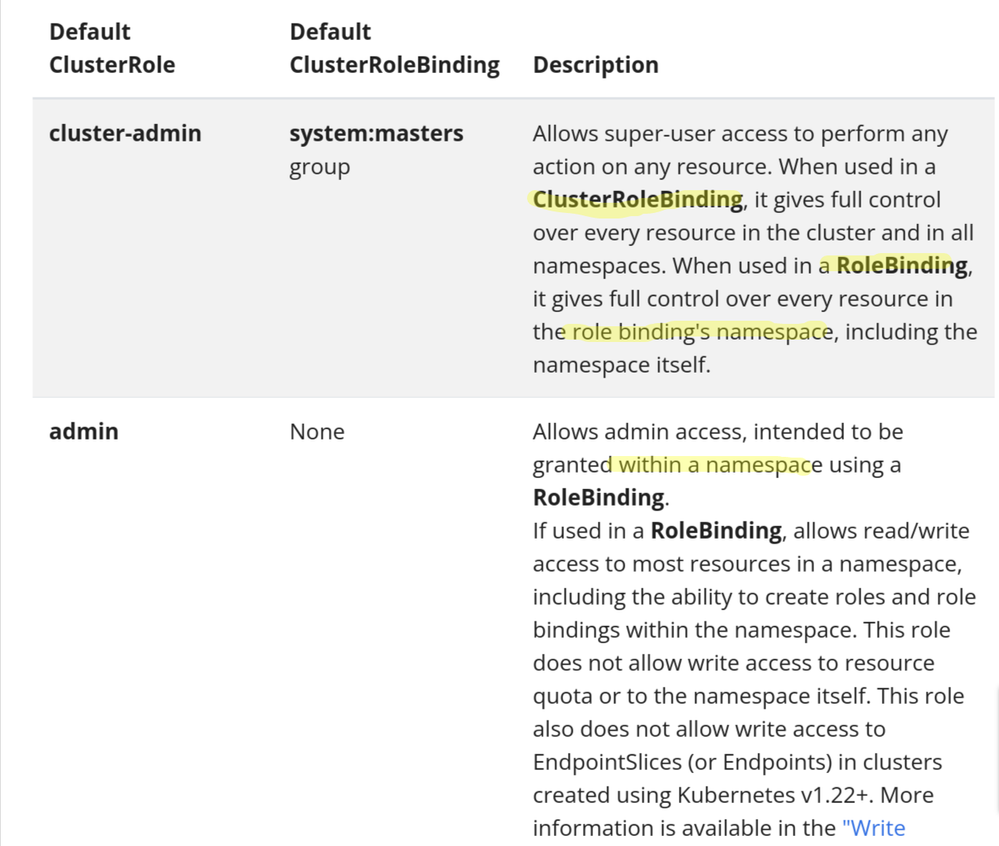
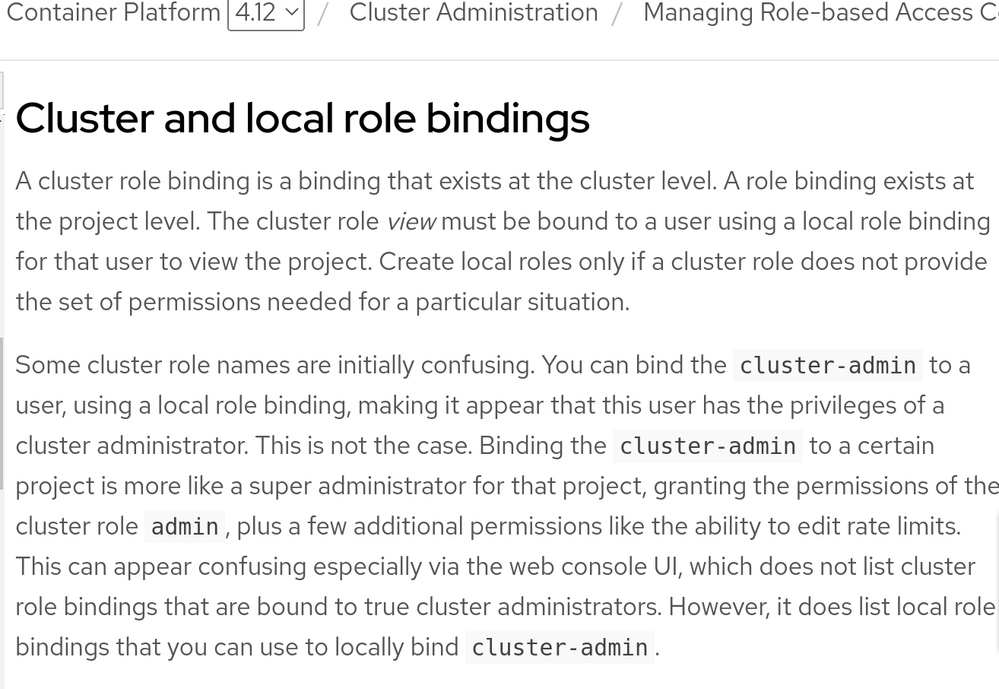
Refer this screenshot for the two "admin" roles :
https://docs.openshift.com/container-platform/4.12/authentication/using-rbac.html
Sorry I do not know about exam questions or any exam scenarios.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 5,082 Views
As per the video in the course, the cluster level roles are: cluster-admin, self-provisioner and cluster-status.
Is there two roles of admin one use: add-cluster-role-to-user and the other admin but use add-role-to-user?
I don't really understand and confused.
About my other question of the self-provisioner role i'm not asking about specific thing that exists in the exam or not or any scenarios available in the exam or not. I'm asking a question with assumption that i'm not sure how to solve it if it appears in the exam and i just need you to tell me the best solution to use.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 5,076 Views
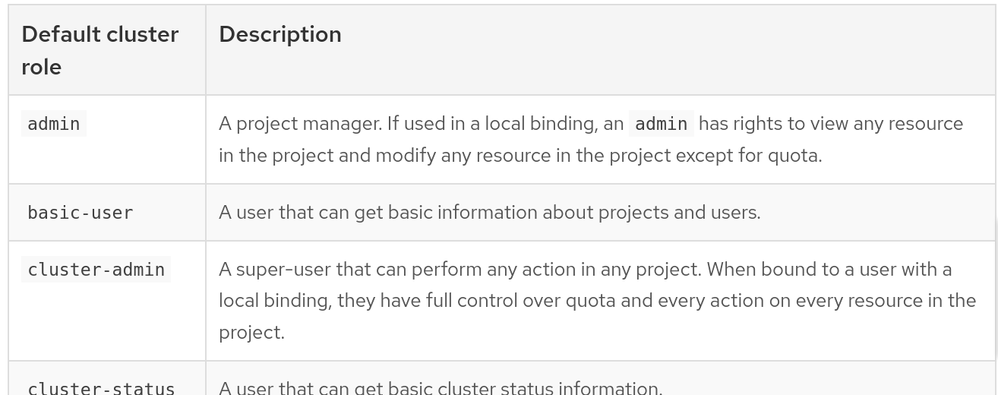
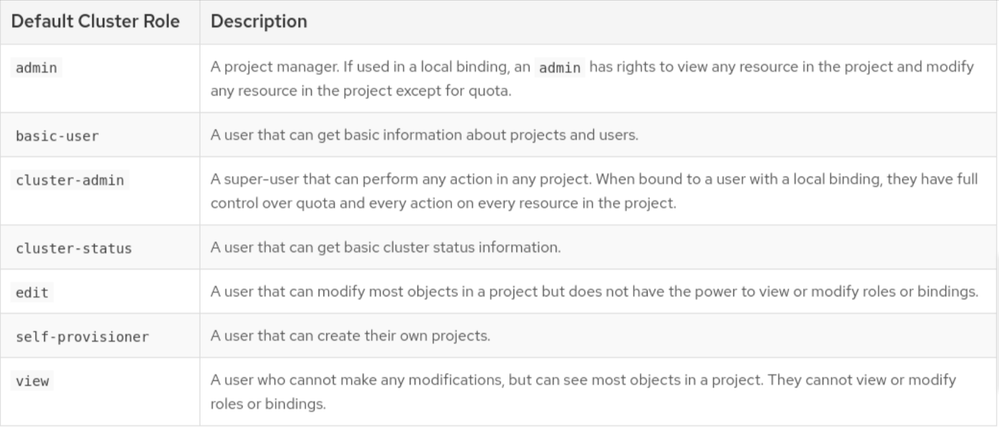
@khokha There are two "admin" ( which contains word admin) roles : Cluster-admin & admin
However, we can have 2 scenarios here :
1. ClusterRole & RoleBinding : Define ClusterRole ( which can be used cluster wide) but attach it to an object in a local namespace.
2. ClusterRole & ClusterRoleBinding : Define ClusterRole ( which can be used cluster wide) but attach it to an object in the entire cluster
Check the previous pic which I attached from OpenShift documentation and read the details https://docs.openshift.com/container-platform/4.12/authentication/using-rbac.html .
Otherwise check this : From K8s official documentation : https://kubernetes.io/docs/reference/access-authn-authz/rbac/
The below ones are the default cluster roles :
Ideally and generally as far as I know : You should use add-cluster-role-to-user if you need to grant a user permissions to access resources across the entire cluster. You should use add-role-to-user if you only need to grant a user permissions to access resources in a specific project.
For your last question : I cannot comment which command you will / should use - but my suggestion is to refer the course book for the same topic in the respective chapter. I am not very sure about the command you mentioned.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 5,072 Views
Thanks for your reply.
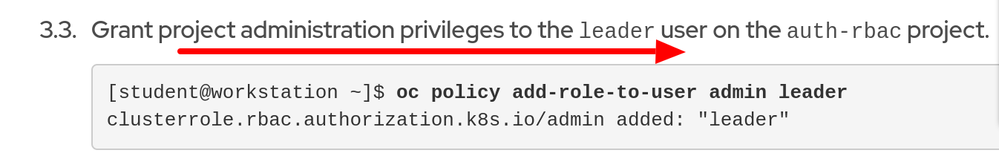
In the G.E. define and apply permissions, step 3.3 the command used to grant admin permisions is:
oc policy add-role-to-user admin UN.
but in the comprehensive review the command used to again grant admin permissions is:
oc adm policy add-cluster-role-to-user admin UN.
Can you explain how the same role is used once with add-cluster-role and other time is used with add-role?
and this command too:
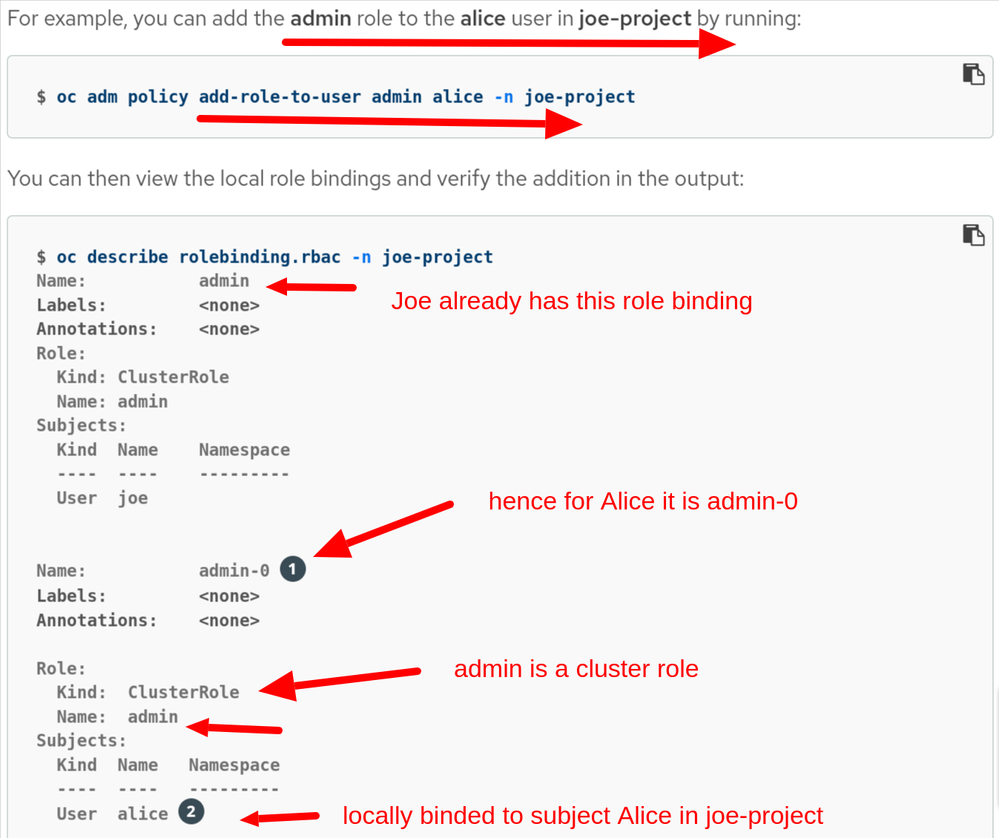
oc adm policy add-role-to-user admin alice -n joe-project
Would i use the previous command too for adding view or edit roles to users or groups on specific projects?
what is the difference when i use command :
oc policy add-role-to-user view UN -n project
Thanks in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 5,067 Views
admin is a default cluster role but when it is locally bounded to a project - ( ch03s04 )
and when it is bounded to cluster wide - (ch10s02)
For your last question , refer this image and see how a cluster role admin is locally binded to user Alice in joe-project
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 4,964 Views
Thanks for your reply.
For granting project administration this would be the same too, if i run:
oc policy add-role-to-user admin alice -n joe-project
as the command you mentioned is: oc adm policy
and in ch03s04 the command is:
oc policy add-role-to-user admin leader
Sorry, but I'm totally confused.
Thanks in advance
Red Hat
Learning Community
A collaborative learning environment, enabling open source skill development.