- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 3,406 Views
A problem with su - command, found in the instructions, and NDG / NetLab+
Apparently, NDG (or someone) changed the root password on the workstation, servera, and serverb machines (and, I'm guessing, serverc and serverd for RH294) in NetLab+.
There are instructions, attached to the labs such as those for RHEL 8, RH124, Chapter 13, Section 2, which instruct the student to use the su - command:
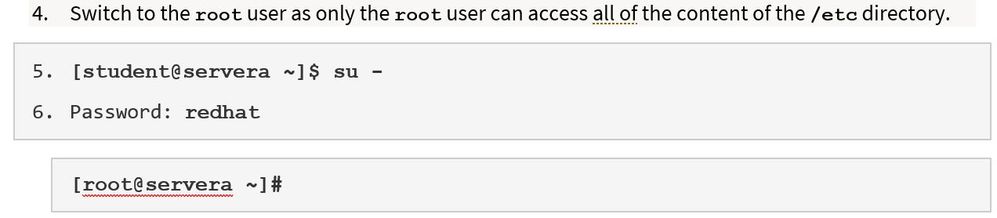
This, of course, will not work unless the root password is known -- and it isn't.
sudo su - will work because the password for student is known:
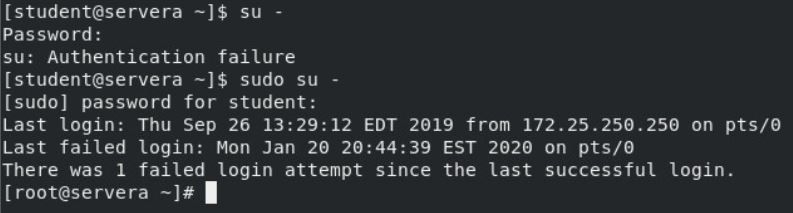
While some may think this isn't any big deal (we can simply instruct our students to use sudo su - all the time), I'd suggest otherwise.
[rant]
I'd guess that for most Red Hat Academies at least 95% of the students are complete newcomers to Linux. To have instructions that are different from what's to be done is less than satisfactory. In my ever-so-humble opinion, it is just plain sloppy (or poorly reasoned) and reflects poorly on instructors and organizations.
Paying attention to details matters. I believe we should do our best to be great examples of that to our students. When they go out into industry, that's exactly what they'll have to do.
Which is why I re-write all the labs and use my instructions instead. (Because we host our own NetLab+, we can remove NDG's instructions.)
I cannot, for the life of me, think of any reason whatsoever as to why NDG would change the root passwords. I mean, come on... sudo su - gives students root access anyway, so there is nothing to be gained by it.
[/rant]
Estrella Mountain Community College
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 3,382 Views
Hi Tracy,
I fully agree that the books are wrong in that way. But instead of showing "su -" or "sudo su -", they should explain what "su -" does and why "sudo -i" is probably what they want.
In real life, companies usually need to ensure that only priviledged staff gains higher access to the system and companies are usually also required to audit these accesses. Sharing a known root password is not a good option here. And since our delegates should learn best practices also, we should encourage them to use sudo whenever possible.
From my practice it usually boils down to create a root password, store that in a sealed(!) safe and create sudo permissions for named admin accounts. The safe is usually an encrypted database and the seal will inform you when someone broke the seal to gain access. There are various products available that work like this.
At my previous employer we switched away from known root passwords. Instead I wrote a short C program that uses pwgen(1) to generate strong 16 char passwords set this for the root user. The program did not gave you the password, but wrote that in the password safe for "root@systemname" and sealed it.
Then we had our named accounts and also the sudoers in a LDAP server, so we centralized the permission management.
Best regards,
Olaf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- 3,355 Views
'I fully agree that the books are wrong in that way. But instead of showing "su -" or "sudo su -", they should explain what "su -" does and why "sudo -i" is probably what they want.'
The chapter on su and sudo do explain these things.
To the rest of your point, Chapter 6, Section 3 says this: "...the password for root should be kept as secure as possible."
-----
My post wasn't to debate su -, sudo -i, sudo su - or any of that; besides, there's nothing to debate -- I agree with you.
One of my points is that the NDG's instructions specifically say to use su -, which requires knowing root's password. But we don't know root's password because NDG changed it.
So: either (1) tell us root's password, (2) change it back to redhat as it is in the physical classroom, or (3) change the instructions... (3) is preferable.
Which led to my rant (and other point): leaving things as they are reflects poorly on me, my institution, NDG, and Red Hat.
So, I write my own instructions and don’t use NDG’s. However, I’m guessing that a lot of Red Hat Academies can’t do that because it means hosting their own NetLab+ system.
This is why I point out these things; I'm trying to help the community at-large.
Estrella Mountain Community College

